The Education strategy of a school would involve various products, solutions that are to be pieced together in harmony to provide a seamless education experience for students and professors. The complete solution and design would depend on the learning strategy and how professors decide that they need to teach.
The first step into designing and implementing a new LMS is what learning strategy we need to follow for our courses within a school.
Selecting a LMS should be done only after answering these three questions.
- Why is a new LMS being considered(i.e., new to eLearning, outgrown the current system, outdated or lack of functionality, too expensive, dissatisfied with vendor)?
- What are the key issues, problems and/or challenges your institution hopes to address with a new LMS?
- Have the staff and budget associated with the task of selecting, implementing, supporting and maintaining a new LMS been identified and earmarked.
Learning Strategy 1. How we plan to deliver programs 2. New learning processes? 3. Success and ROI of LMS 4. Pedagogical approaches and models of the institution
Why is a new LMS being considered?
We must address the following with this new LMS
- Course management for Faculty & Students.
- As a means to deliver content digitally to students
- Mobile Learning capabilities
- Ability to integrate with our planning systems.
- Ability to do distance learning and eLearning effectively.
- Simulations and Aids to teaching
Course management for Faculty and students
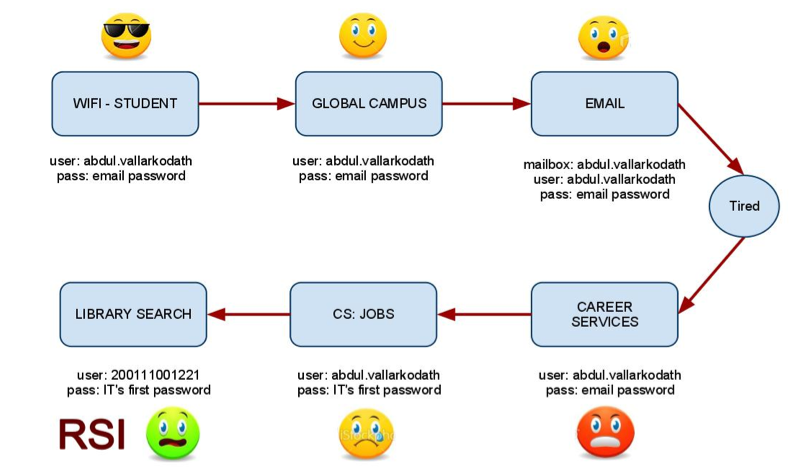
The current solution of Global campus using sharepoint leaves much to be desired. The concerns are
- There are over 800 live independant sites on sharepoint for Global campuses with no central control
- Usability of content is very low
- Cost of redesigning and recreating a new sharepoint site is very high and this cost climbs each year with more custom programs.
- Integrations with back end systems like faculty planner is virtually non-existent and any efforts currently is quite expensive.
- Faculty (and also students) have to navigate through a series of links before finally arriving at a relevant course page.
Apart from resolving the issues of the current platform, we need the following features to be more productive and usable.
- Accessibilty from multiple devices invluding, iOS, Android, Mac, Windows, Linux etc.
- Ability to do distance learning or eLearning effectively Traditionally we have been a program with a heavy focus on in-person training. Case based methodology to a big extent requires this.
We have distance learning modules focused on conducting a case based discussion using newsgroups. The newsgroups had several significant considerations:
- Replicate classroom discussions on an online asynchronous platform.
- Discussion should persist over a period of time
- Having prolonged discussions gives an opportunity for everyone to participate
- This helps professors to get to know students and if needed give individual help to them.
- Gives an opportunity to understand and thus help students who do not participate much in class.
- Ability to share links and contents and other attachments with students
- Possibility of different boards for different topics gives the ability to discuss different things in different places making sure that content is well organized.
- Every class and every case has its own board
- Nested replies and multi-level threads are great. It also allows two people to argue/debate something out, without hindering others (unlike a class discussion)
- The newsgroups are significant investment of professor time.
Thus, eLearning platforms, must strive to enable an offline classroom discussions and help aid in the case based methodology that a school is built on.
Distance learning platforms should also be quick courses we could deliver as a course pills. With its own Content and (maybe) and exam to verify appropriateness. These are especially attractive for soft skill course like Company Ethics etc. Quick course in Accounting principles of quantitative methods. These pills could contain multimedia material, video, audio and text along with an interactive element attached to it.
As means to deliver content digitally to students With the flourish of Mobile and table devices with incredible capabilities which are carried around by users (students, staff, faculty) wherever they go, delivering materials digitally is a no-brainer.
An LMS should enable the distribution of content digitally to users in a way such that relevant content is delivered through an open protocol to students. The following contents should be covered:
- Cases
- Technical Notes
- Case supplemental videos
- Other reading material.
- Annexes of cases
- Exercises and assignments.
The LMS should allow the following
- a school Back-office staff to upload and organize the content integrated with the current systems that are used to deliver content.
- Professors should need to update any content on their sessions at any time to allow flexibility. e.g. new article in today’s newspaper, change in case etc.
- Relevant content access. People with the right permissions can update, create content for courses.
Improved usability in our course management systems
Usability should be a key aspect for a Learning management systems.
The LMS should be platform independent for users. Access should be available with more or less same functionality with the following devices
- Windows PC
- Mac OSX
- Linux
- Android Phones & Tablet
- iOS Phones and Tablets
The LMS should ensure compatibility and elegant delivery on the following browsers
- Firefox
- Google Chrome
- Safari
- Internet Explorer 9+
Mobile Learning Capabilities
“Learning that happens across locations, or that takes advantage of learning opportunities offered by portable technologies”
Key capabilities in mobile can involve:
- Delivery of learning materials, including transcripts, audio or videos of lectures for review. (Integration of LMS having a mobile ui)
- Self-assessment and quiz aids
- Access to assignments and syllabi
- Creation of user generated content for sharing or later referral
- Campus tours or navigation and resources
- Access to grades
- Registration for classes
- In-class audience response and polling
- Access to faculty and fellow students
- Easy access to coaches, mentors and tutors
- Social networking, such as blogs, Facebook or Twitter
- Campus information - contacts, emergency exits, security contacts
- eBook Reader
Examples of use of social networks like facebook/twitter or socialcast.
- A professor in accounting can post an accounting problem and the first to give a solution would get extra points.
- Professors and program coordinators can use this for course and class announcements.
Important questions to answer
- How could faculty use mobile capabilities to enhance classroom learning?
- What capabilities would be of interest to students and prospective students?
- How can ubiquitous and asynchronous connectivity better enable faculty and student interaction?
- What campus services will help students be more productive or safe?
- What materials are already on hand that could be made easier to access via mobile devices? Does content already exist in another form?
- What network will be used for distribution? What actions or activities will need to be tracked?
- What mobile tools will the student be using upon graduation that they should gain experience with now?
- How will mobile learning integrate with other systems on our campus or does it need to?
- Who will handle any needed user support?
- Are there partners or potential funders for our initiative?
- How will this new opportunity be communicated/marketed? Simulations and other aids to teaching Simulations are used to aid teaching in various courses. Examples include the beer game, ipade project etc.
Current Identified needs include the following: 1. Simulation of the Beer Game. 2. In Company Projects, off-campus classes etc.
Key Issues at a school we want to tackle
Issues we need to consider
- Security for our content.
- Content have to be always:
- Password protected
- Contain a social watermark (e.g. “This content is delivered to MBA 2010 - Section B”)
- Ease of access through multiple platforms, through open protocols
- Ability to let consumerism take its way. Let the open market guide users to selecting applications they prefer.
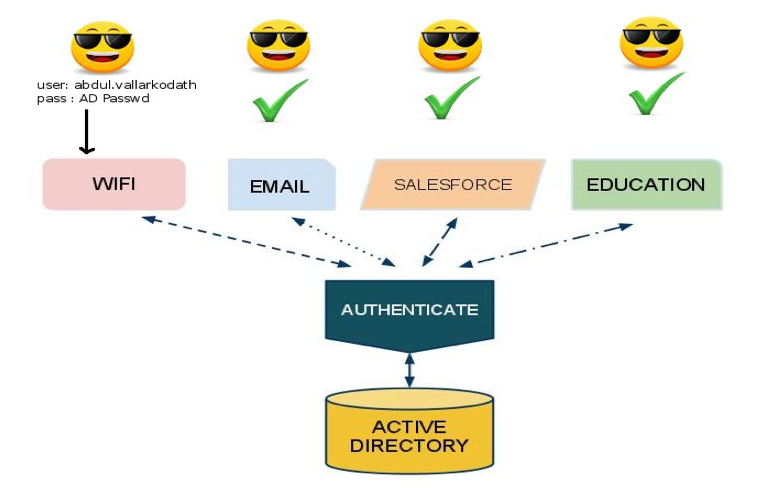
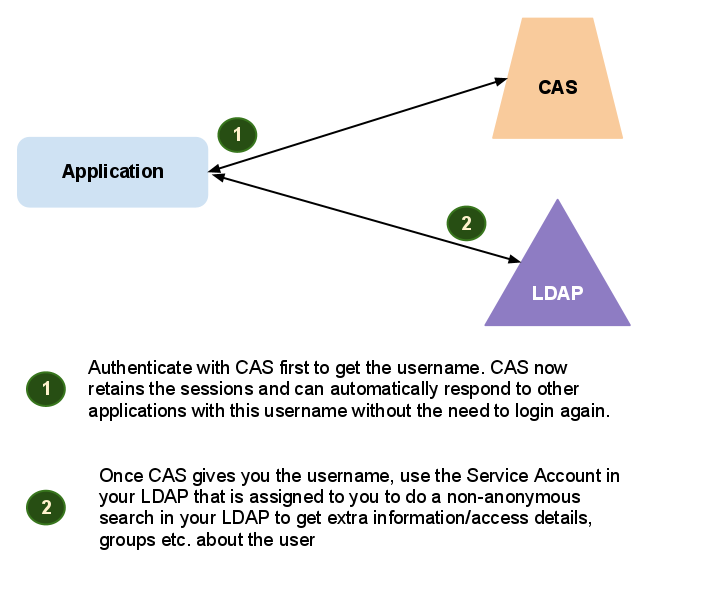
Integrations
We need to be able to customize php applications and use them integrated with blackboard. Embed php applications.
Third party applications include, webex, apple, etc.